Top Industries That Require Data Protection
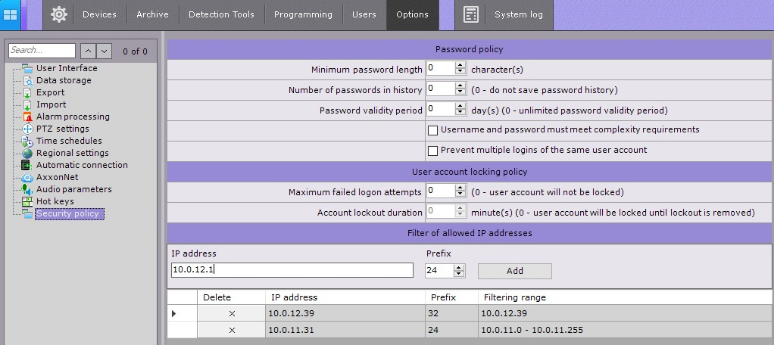
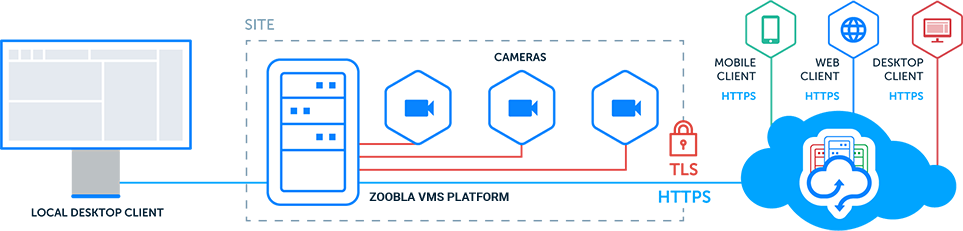
- The bitter but straightforward reality is that individuals, businesses, and industries of all types are vulnerable to data security issues
- Many of us know people who continue to forego locking their devices or use extraordinarily common and predictable passwords to protect their computers or online accounts. Similarly, a variety of businesses do not prioritize the necessity of data security, or they engage in half-measures—dedicating too few resources to their efforts at protecting data.
- Many of us know people who continue to forego locking their devices or use extraordinarily common and predictable passwords to protect their computers or online accounts. Similarly, a variety of businesses do not prioritize the necessity of data security, or they engage in half-measures—dedicating too few resources to their efforts at protecting data.